Azure App Configuration
This describes the steps required to setup an App within the Azure Active Directory required when either an Smtp or POP3 server will send mail via or access an Office365 mailbox.
Please note the instructions below are the broad steps required based on a typical Office365 subscription.
The steps may vary dependent on the level of subscription and administrative privileges and are not an exhaustive discussion of Azure permissions.
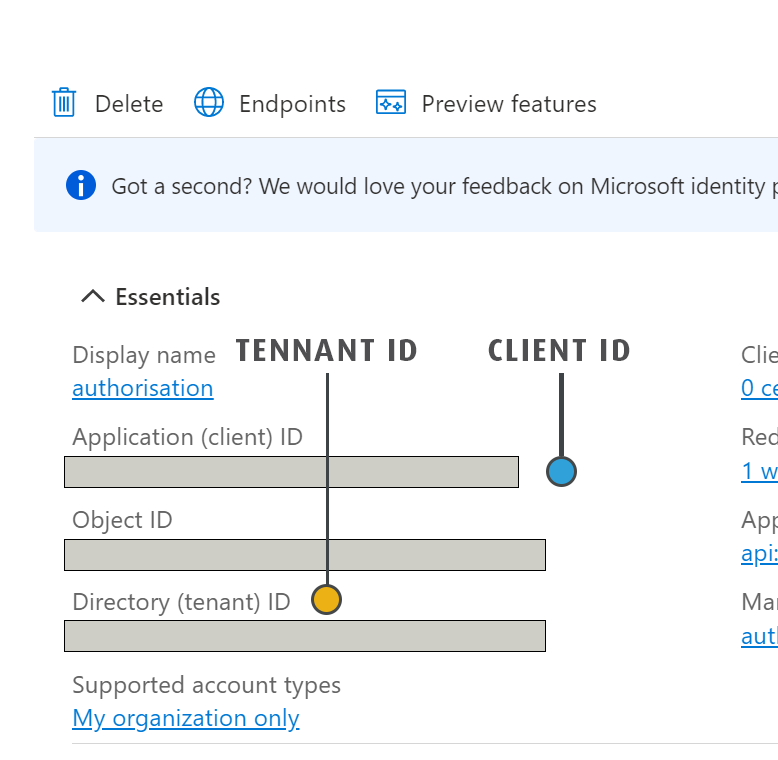
Following the App Creation, you will have noted three values (Azure Tennant Id, Azure Application/Client Id, Client Secret) which are used when setting either the Office365 Smtp Server or Office365 POP3 Server servers.
Azure Active Directory Login
-
Login to the Azure Active directory with a user which has admin rights i.e. rights to create an App in the Azure Active Directory.
-
Click the App Registrations.

Create An App Registration
-
Click the New Registration button at the top.
-
Click Authentication and add a new Redirect Uri
https://authorisation.realisable.co.uk/OAuthCallback
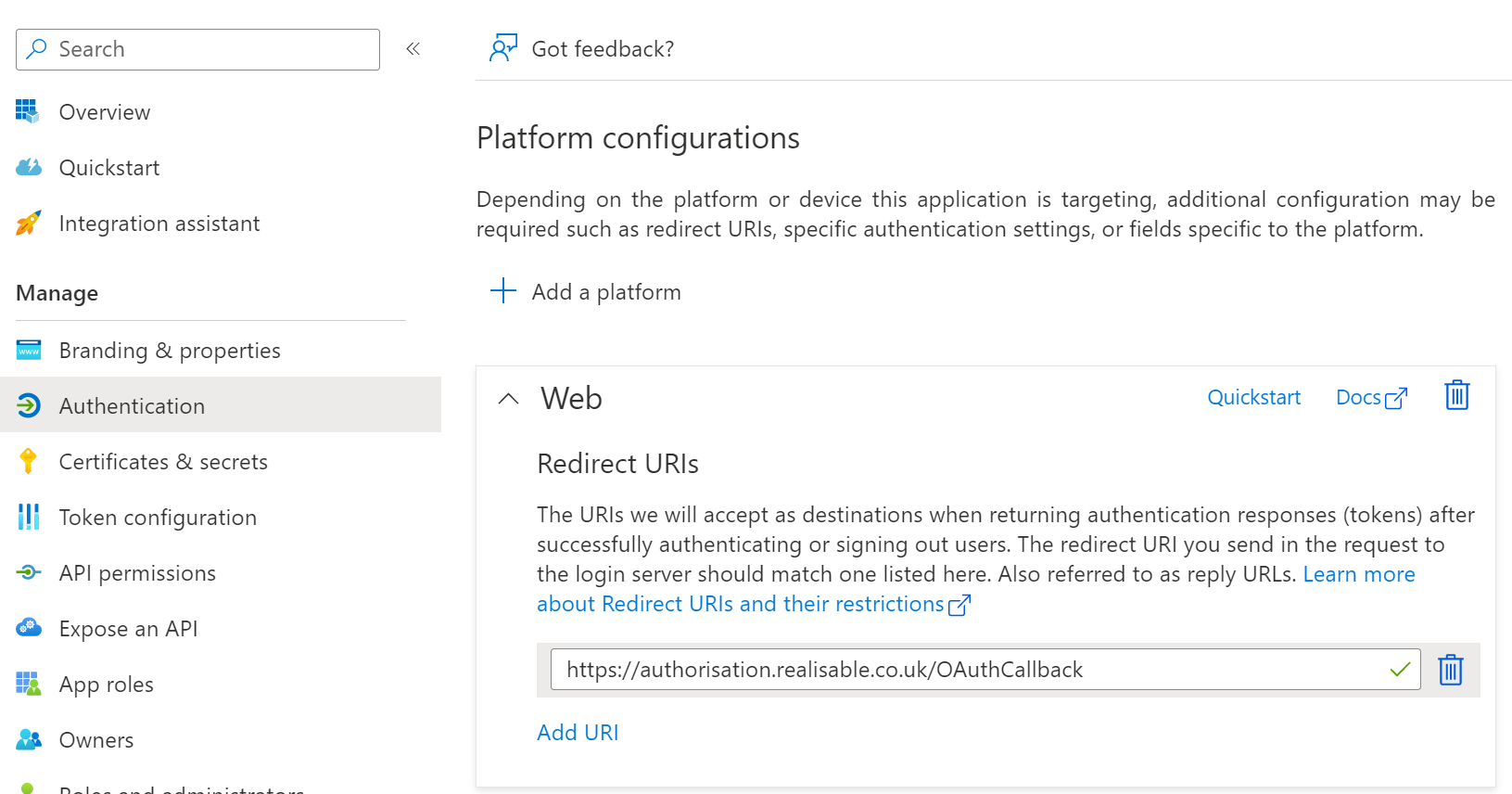
Then press Save.
-
Click Certificates and secrets, then Client secrets, then New Client Secret.
-
Enter a description and select an expiry, then press Add.
A short expiry will mean you will need to re-authenticate often.

-
Make a note/copy of the Client Secret (it will only be shown once). If you do not copy the value you will need to recreate a new secret.

-
Click API Permissions.

-
Click Add Permission.

-
Click Delegated Permission.
-
Click/select Microsoft Graph.

-
In the search bar search for 'offline_access' and select the checkbox.

-
Repeat the step above to add the following permissions.
- openid
- User.Read
- Smtp.Send
- This allows users to send email.
- POP.AccessAsUser.All
- Only required when requiring access to an Azure POP3 Mailbox.

-
Click Overview.

-
Note the Tennant ID and Application ID values/GUIDs.